The Identity Gap: 2025 Snapshot What’s Still Missing in Enterprise Identity Security

About the Data in This Report
Orchid Security leverages the latest advancements in observability, prompt engineering, and large language models to intimately analyze application behavior and evaluate identity security flows.
The applications analyzed have been deployed throughout North America and Europe, spanning industries including financial services, healthcare, retail, manufacturing, energy and more. The findings in this report are based on the anonymized and aggregated telemetry collected through Q1 2025.
Our goal is to shed light on the most common and persistent gaps in enterprise identity security, guiding organizations on where to strengthen identity security posture. While many organizations believe they have "identity covered," our findings show that beneath the surface, critical flaws remain.
We hope this report serves as a wake-up call for practitioners and decision makers.
Understanding, let alone maintaining, identity security posture across any large organization- with its diverse and always evolving application estate- is a constant challenge.
Remember, that estate includes applications created by different developers, at different times- when technology, regulations and cyber risk were different- and even by different organizations if acquisitions were part of the growth strategy.
Any approach, but especially an automated one, that provides a comprehensive and accurate view into the true state of identity, is hugely valuable to CISOs. Especially when it can surface all of the identity flows coded in each application. We know that many threat actors are adept at finding the alternate or forgotten ways into our organizations, and this report highlights the most common exposures we need to look out for (and address).
The insights shared here are instructive for every cyber security professional.
Executive Summary
While many organizations believe they have 'identity covered,' our application-level assessments consistently expose critical weaknesses from mismanaged credentials and insecure authentication flows to improper protocol usage and gaps in enforcing essential controls.
The most common identity security exposures, with their prevalence, were:
- 48%
Storage of hard coded, cleartext credentials or use weak hashing
- 44%
Authentication paths that bypass the corporate Identity Provider
- 40%
A lack of baseline controls like rate limiting, account lockout and password complexity
- 37%
Outdated or non-standard authentication protocols
- 37%
of applications failed to enforce access controls fully or at all

Introduction
It’s only a few months into 2025, but one thing is already clear: stolen credentials remain one of the easiest and most effective ways attackers break in.
Credential-Based Breaches:
2025 Timeline
- January 2025
PowerSchool Breach
Cybercriminals reportedly used stolen credentials to access a support portal that lacked MFA, exposing sensitive student and parent data.
- March 2025
Jaguar Land Rover Incident
A threat actor used stolen credentials to infiltrate the company’s Jira system, allegedly stealing over 700 internal documents.
- April 2025
Verizon Data Breach Investigations Report
Verizon Identifies Stolen Credentials as Top Breach Entry Point In their latest report
Why do stolen credentials remain such a reliable tactic for attackers year after year? In many large enterprises, complex and aging systems make it difficult to implement consistent identity controls and maintain visibility across every access path.
Anonymized and aggregated data from Orchid's identity security orchestration platform shows that foundational identity weaknesses persist across Fortune 500 organizations in both the U.S. and Europe.
Key Findings
1. Credentials Stored Insecurely
A foundational control properly securing credentials within applications is often ignored. Nearly half the analyzed apps still rely on hardcoded or improperly stored credentials.
What we found:
- Credentials embedded in codebases, configuration files or automation scripts.
- Frequently justified by: "Only humans use the IdP. These are system-to-system paths."
- Especially common in machine/service accounts and NHI (non-human identity) scenarios.
Why it matters
These credentials are easy to harvest, hard to rotate, and often shared across systems. If exposed, even briefly, they can become high-impact footholds for attackers and are a common vector for lateral movement and persistent access.
2. Partial use of Identity Providers (IdP)
A key control routing all authentication through a centralized identity provider is inconsistently applied. In 44% of cases, applications had at least one access path that bypassed the enterprise IdP.
What we found:
- Direct or local login paths unmanaged by global policies.
- Often justified with: “We needed to provide access to contractors or vendors.”
- Common in apps with standalone or legacy directories.
Why it matters
These paths tend to be complete blind spots, making them ideal targets for attackers to exploit in full stealth using commonly outdated or forgotten credentials.
3. Missing Baseline Identity Controls
Essential controls like login rate limits, account lockouts, and password complexity are missing in many applications. 40% of systems lacked one or more of these protections.
What we found:
- Missing enforcement for basic login hygiene.
- Variability across dev teams and codebases.
- Commonly in internally or legacy developed tools.
Why it matters
Without these controls, attackers have more opportunity to brute-force or test stolen credentials.
4. Outdated Authentication Protocols
Many enterprises continue to rely on outdated authentication protocols. 37% of cases included insecure or nonstandard approaches.
What we found:
- Use of FTP, NTLM, and custom token systems.
- Common in niche or legacy application stacks.
- Often a byproduct of tech debt or developer autonomy.
Why it matters
These protocols are harder to secure, less visible to monitoring tools, and widen the organization’s attack surface.
5. Access Control Enforcement - a Hygiene Failure.
Even after authentication, 37% of applications skip the hygiene of access control enforcement, lacking critical guardrails like role-, attribute- or policy-based access control. This foundational failure erodes least privilege, silently turning routine identities into high-value targets, risking breaches like Jaguar Land Rover’s 2025 incident and violating PCI-DSS, SOC 2, ISO 27001, GDPR, and HIPAA.
What we found:
- Instances where "all users" were allowed full access
- Applications with no permission checks
- Misconfigurations that allowed anonymous access
Why it matters
Weak access controls erode least privilege, letting users and accounts gain excessive access over time, turning them into high-value targets. Worse, these failures are silent seeming compliant until a breach or audit reveals the gaps.
Regional Trends
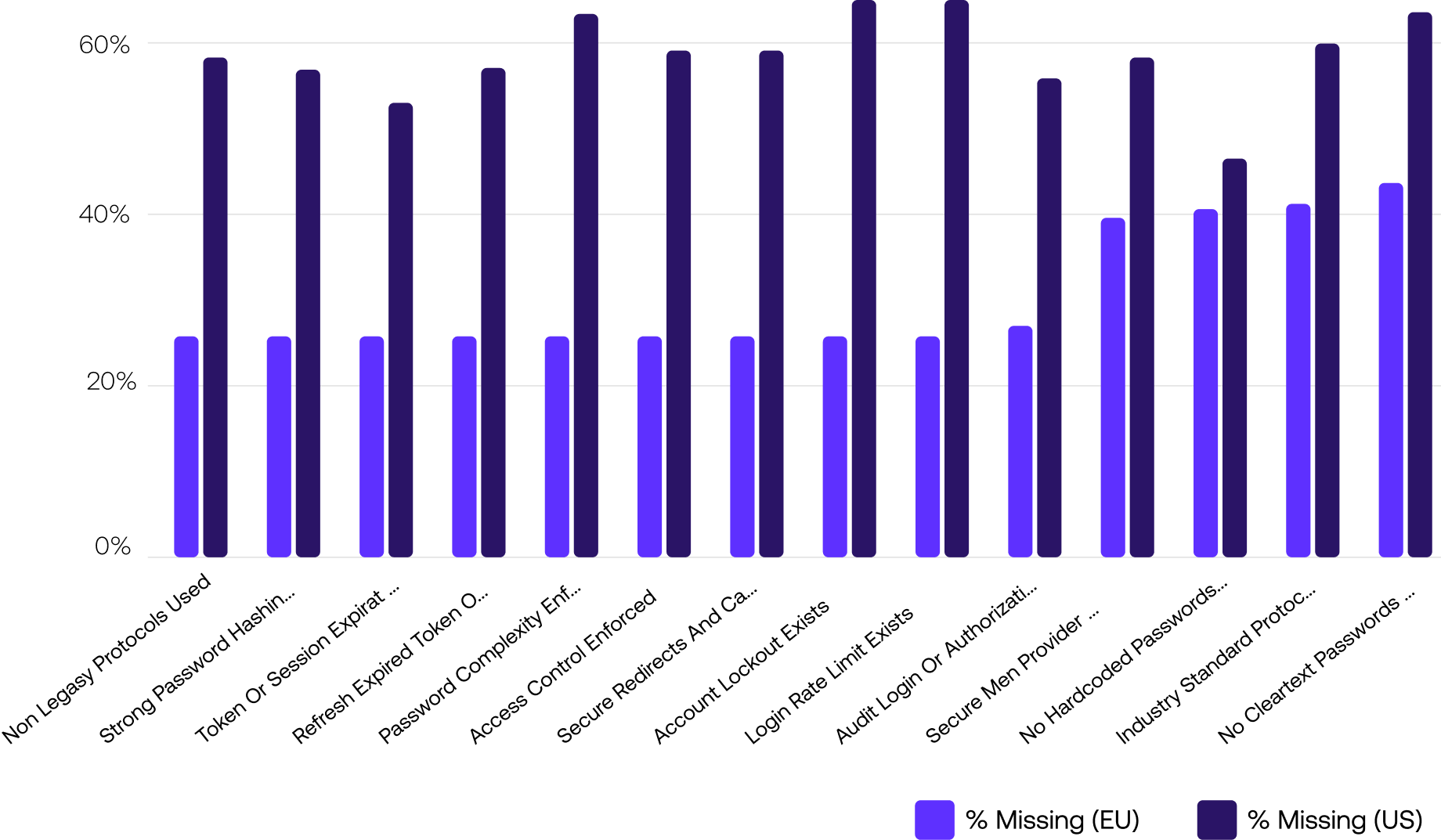
As final observations:
Geography does seem to influence practices. European development teams appear relatively more disciplined in implementing foundational identity controls. Anecdotally, this may stem from the structured, though often restrictive use of Active Directory for both authentication and authorization.
Despite these regional differences, significant blindspots and gaps in identity control implementation remain widespread
Given the cyber and compliance risks associated with missing identity security controls, we strongly recommend that enterprises regularly and more comprehensively evaluate their identity security posture across all applications and identity flows. This evaluation should go beyond established best practices, incorporating deep, code-level and engineering-driven reviews to uncover hidden identity mechanisms and overlooked vulnerabilities.
For actionable guidance, refer to our Checklist to Identify the Top Missing Identity Controls.
Checklist to Identify the Top Missing Identity Controls
Download Checklist
How Orchid Can Help
Discovery and Gap Analysis: Continuous Visibility Beyond the Known
Orchid delivers continuous, telemetry-driven visibility into identity implementations across all automatically discovered applications regardless of geography, technology stack, or existing compliance knowledge. This capability empowers organizations to uncover both commonly missed controls and hidden identity mechanisms that conventional audits and reviews often fail to detect.
No Prior Context or Manual Input Required
Unlike traditional assessment and onboarding processes that rely on interviews, documentation, or involvement from app owners or developers, Orchid's analysis is entirely autonomous. It requires no prior data points, tribal knowledge, or manual onboarding, making it ideal for large, fast-changing environments.
Save Time, Save Money — Harness Your True Identity Landscape
By eliminating the need for human-led discovery, context-gathering, or code walkthroughs, Orchid significantly reduces the time and cost of identity posture management. It accelerates both discovery, gap analysis and remediation cycles including onboarding, freeing up security teams and engineering resources to focus on higher-impact work while utilizing the organizational siloed identity tools.
Checklist, Fully Covered
Our platform aligns directly with the Checklist to Identify the Top Missing Identity Controls and many more providing instant, actionable insights on where your applications stand and what needs attention.










.png)
.png)




